引言
Welcome to the comprehensive overview of the "2024 Latest Cars, Analysis of Access Security Solutions: Cyber Edition 94.737". As we dive into the intricacies of safety in vehicles integrating state-of-the-art cyber features, it is important to shed light on how these innovations impact drivers and passengers alike. Technology has advanced significantly over the years, but so has the need for robust security measures that ensure user safety and data privacy.
背景与市场趋势
In recent years, automotive manufacturers have been incorporating cutting-edge cybersecurity features due to rapid technological advancement and increasing demand from consumers who prioritize digital safety. The market trend heavily leans towards cars equipped with real-time monitoring systems, smart recognition services, and secure connectivity protocols.
- Vehicle Safety Standards are evolving to include not just physical protection features but also digital safeguards against sophisticated hacking attempts.
- The rising importance of electric vehicles adds another layer to vehicle security, as they pose unique challenges in safeguarding energy management and power systems.
- The integration of AI and autonomous driving technology mandates a reevaluation of regulatory compliance and testing methods for digital resilience.
先进防护功能
Automated defensive multiplier functionalities play a crucial role in today's smart cars. Below are some standout features found in our selectcy54d7bseries of 2024 vehicles:
- Encryption-hardened Operating Systems - At the heart of every car, lies its central processing system which communicates with each module through an encrypted operating system to ensure data confidentiality and integrity.
- Hybrid Authentication Mechanisms - In addition to traditional key-based ignition, new vehicles support entry through biometric recognition such as fingerprint scans or facial recognition.
- Threat Detection & Response Systems - Advanced intrusion detection systems alert you to any possible attack vectors like unauthorized access attempt or illicit data exfiltration.
- Network Segmentation - Strategic partitioning within the networked components both inside the vehicle and between the vehicle and external entities facilitate stricter control over sensitive information flow.
易受攻击的环节识别
A thorough examination of potential weak points is essential before implementing protective measures. As the automotive industry adopts connected technologies, some elements might prove susceptible:
- Physical Components that accept wireless signals may be prone to signal interference or spoofing attacks, requiring enhanced shielding and authentication to minimize vulnerabilities.
- Remote Access Interfaces are a double-edged sword - remote operations can be incredibly convenient while simultaneously presenting risks should they fall into malicious hands.
- Components Interaction Floorings – as multiple electronic control units (ECUs) communicate with each other, there's a heightened risk of cross-contamination if one unit becomes compromised.
存储与数据隐私
Data storage solutions in modern vehicles must handle personal passenger info securely, along with operational diagnostics and predictive analytics. The following are parameters to ascertain data integrity:
- Secure Data Flow Management - How data circulates throughout the car infrastructure must align with strict cyber governance, ensuring accountability.
- Consent-Based Processing - Users should be made aware of what data is collected and given an option to opt-out where nonessential.
- Privacy by Design - When developing software and hardware capabilities, it is paramount to prioritize privacy considerations during all stages of production rather than treating them as afterthoughts.
现行法规与合规性
Noting the adoption of the latest standard SCADA Driver Privacy Act 2023, automakers are required to conform to comprehensive regulatory cyber practices. Compliance considers:
- Regulatory Requirements: Complying with global cybersecurity norms becomes obligatory, whether ISO/SAE 21434 or national-specific guidelines.
- Periodic Gap Assessments: Regular evaluations should be conducted to map out potential gaps in compliance that could expose vehicles to threats.
- Due Diligence: documenting measures taken to identify, prevent, manage, and prosecute those attempting to breach cybersecurity measures is mandated.
未来技术展望
The auto industry is poised for further advancements in providing safer and more secure mobility solutions. Future developments will focus on:
- Blockchain for immutable records - Immutability ensures transparency and validation when tracking maintenance history and digital IDs.
- Quantum Resistant Cryptography - Preparing defenses against quantum computers that may break current encryption standards.
- Sensor Data Integrity Verification - Rigorous checks to counteract manipulated inputs like GPS, speedometers, and radar systems from autonomous-driving supports.
结束语
As the automobile sector ventures deeper into the tech-driven age, the quest for top-tier access security persists. For enthusiasts looking to drive with confidence in 2024 vehicles, our rigorous evaluations strive to provide peace of mind. Through industry-leading solutions, continuous innovation, and diligent assessments, the future of car security promises to uphold individual safety and adhere strictly to best practice standardizations.

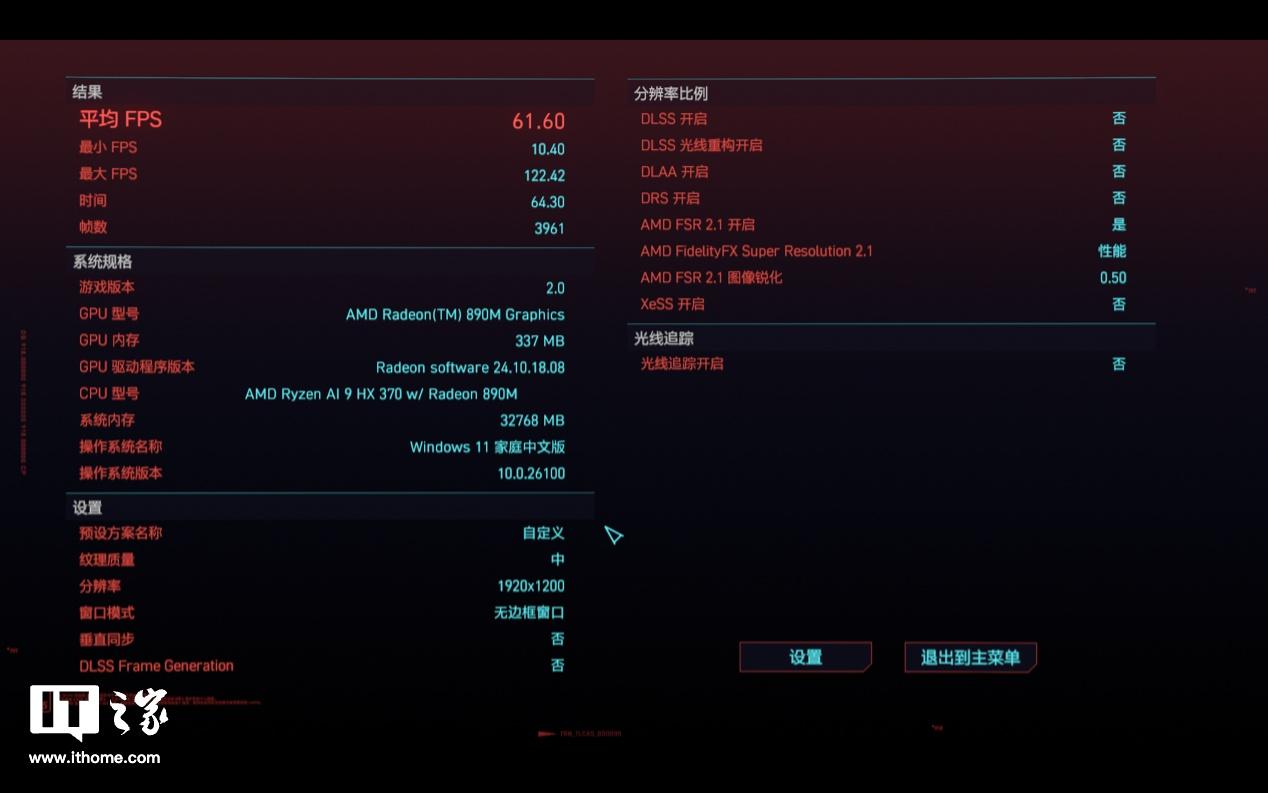
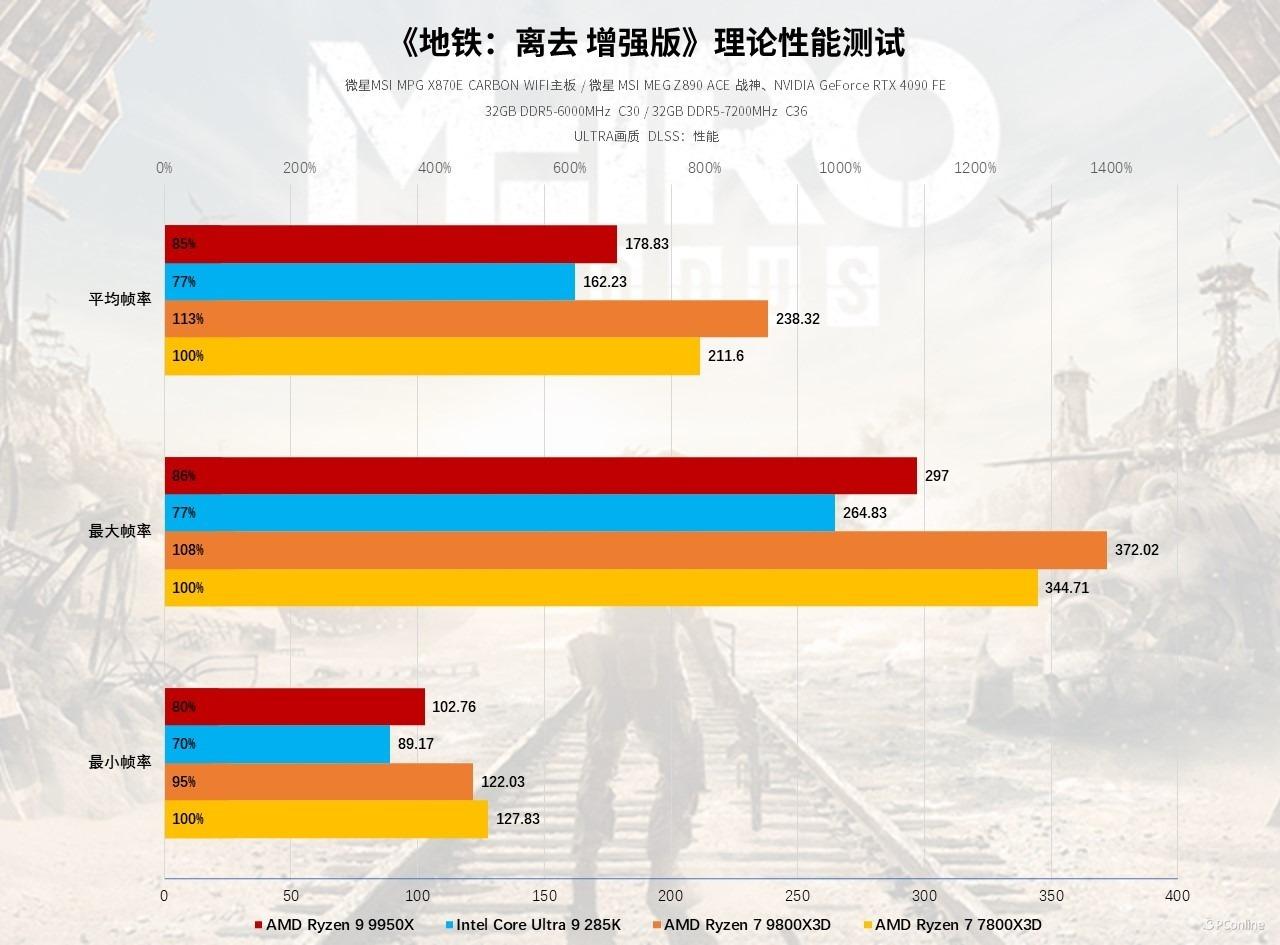
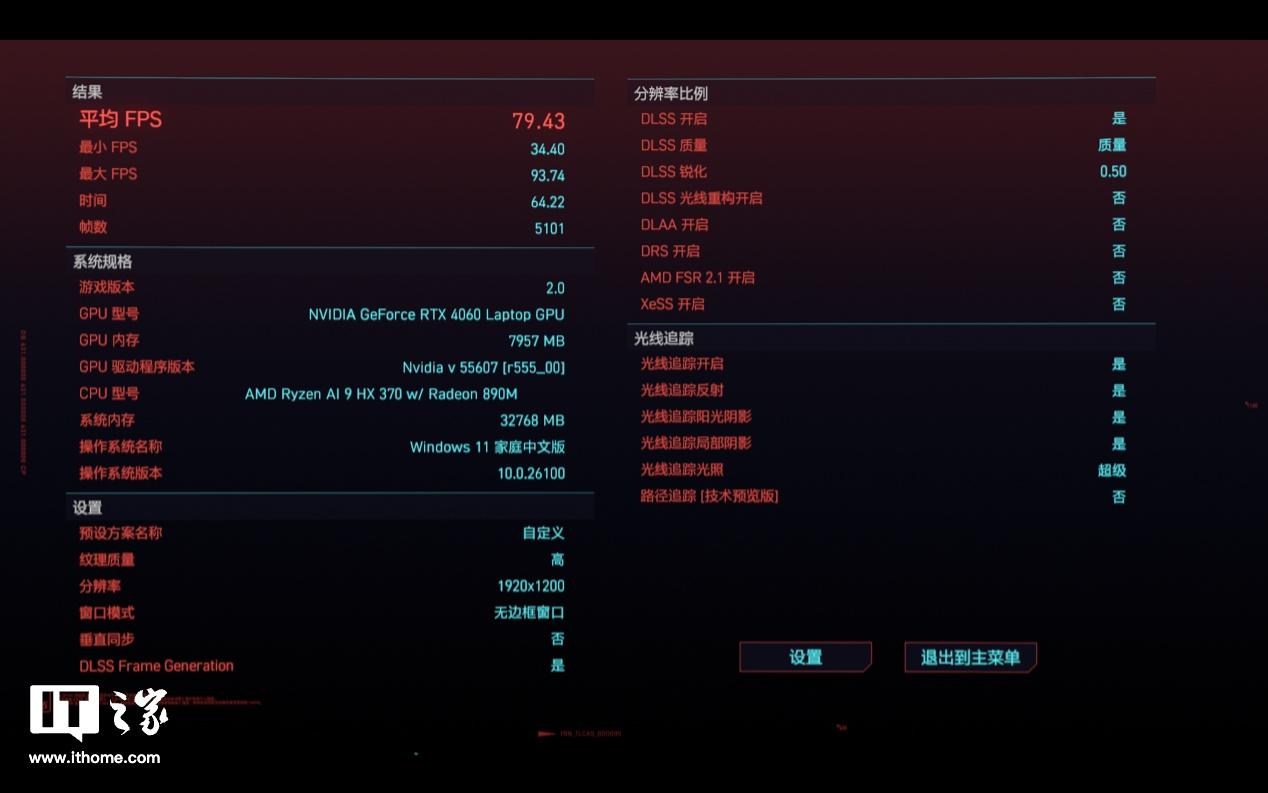






 京公网安备11000000000001号
京公网安备11000000000001号 京ICP备11000001号
京ICP备11000001号